gRPC is a high-performance, language-agnostic remote procedure call (RPC) framework developed by Google. It’s designed for efficient communication between microservices and is based on the HTTP/2 protocol. While gRPC offers impressive performance out of the box, it’s essential to conduct performance testing to ensure your services can handle real-world loads effectively. In this comprehensive guide, we’ll explore the importance of performance testing for gRPC services and provide code examples and best practices to help you get started.
Setting Up a gRPC Service for Performance Testing
Before we dive into performance testing, let’s set up a simple gRPC service and client for demonstration purposes. We’ll use Python and the gRPC library for this example.
Installing gRPC for Python
You can install the gRPC Python library using pip:pip install grpcio
| pip install grpcio |
| pip install grpcio-toolip install grpcio-tool |
Creating a Simple gRPC Service
Let’s start by defining the service interface in a Protocol Buffers (protobuf) file:
| syntax = "proto3"; |
| package calculator; |
| service Calculator { |
| rpc Add (AddRequest) returns (AddResponse); |
| } |
| message AddRequest { |
| int32 num1 = 1; |
| int32 num2 = 2; |
| } |
| message AddResponse { |
| int32 result = 1; |
| } |
Now, generate the Python code from the protobuf file:
| python -m grpc_tools.protoc -I. --python_out=. --grpc_python_out=. calculator.proto |
Implementing the gRPC Service
Let’s implement the gRPC server:
| import grpc |
| import calculator_pb2 |
| import calculator_pb2_grpc |
| class Calculator(calculator_pb2_grpc.CalculatorServicer): |
| def Add(self, request, context): |
| result = request.num1 + request.num2 |
| return calculator_pb2.AddResponse(result=result) |
| def serve(): |
| server = grpc.server(grpc.ThreadPoolExecutor(max_workers=10)) |
| calculator_pb2_grpc.add_CalculatorServicer_to_server(Calculator(), server) |
| server.add_insecure_port("[::]:50051") |
| server.start() |
| server.wait_for_termination() |
| if __name__ == "__main__": |
| serve() |
Creating a gRPC Client
Now, let’s create a simple gRPC client to interact with the service:
| import grpc |
| import calculator_pb2 |
| import calculator_pb2_grpc |
| def run(): |
| channel = grpc.insecure_channel("localhost:50051") |
| stub = calculator_pb2_grpc.CalculatorStub(channel) |
| request = calculator_pb2.AddRequest(num1=5, num2=3) |
| response = stub.Add(request) |
| print("Response:", response.result) |
| if __name__ == "__main__": |
| run() |
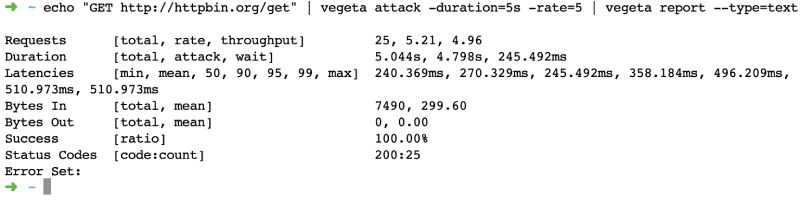
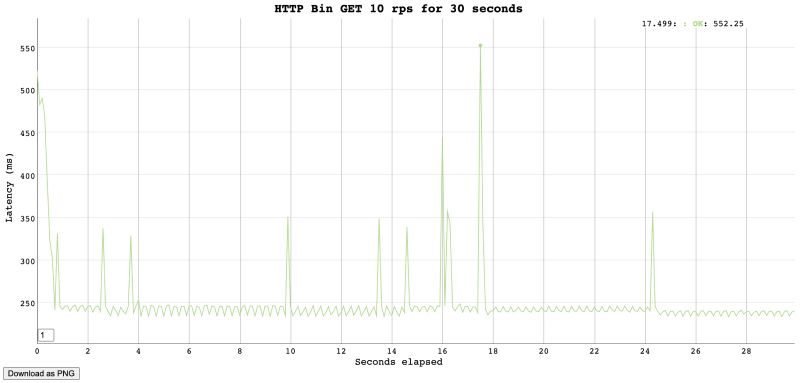
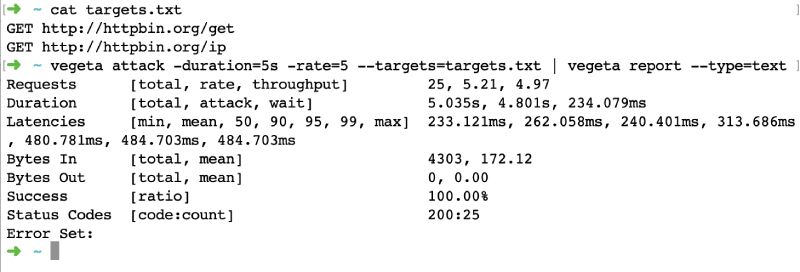
Conducting Performance Testing
Now that we have our gRPC service and client set up, let’s conduct performance testing using two popular tools: Locust and Gatling.
Performance Testing with Locust
Installing Locust
You can install Locust via pip:
pip install locustWriting a Locust Test Script
Here’s a Locust test script that simulates multiple users making gRPC requests:
| from locust import HttpUser, TaskSet, task, between |
| class GrpcUser(HttpUser): |
| wait_time = between(1, 5) |
| @task(1) |
| def add_operation(self): |
| payload = {"num1": 5, "num2": 3} |
| self.client.post("/calculator.Calculator/Add", json=payload) |
Running the Locust Performance Test
You can run the Locust test with the following command:
| locust -f locustfile.py --host=http://localhost:50051 |
Locust will start a web-based UI on `http://localhost:8089`, allowing you to configure and run your performance test.
Performance Testing with Gatling
You can download Gatling from the official website (https://gatling.io/download/) and follow the installation instructions.
Writing a Gatling Simulation
Here’s a Gatling simulation script for testing gRPC services:
| import io.gatling.core.Predef._ |
| import io.gatling.http.Predef._ |
| class CalculatorSimulation extends Simulation { |
| val grpcConf = http |
| .baseUrl("http://localhost:50051") |
| .header("Content-Type", "application/grpc") |
| val scn = scenario("gRPC Performance Test") |
| .exec( |
| http("gRPC Add") |
| .post("/calculator.Calculator/Add") |
| .header("grpc-encoding", "identity") |
| .header("TE", "trailers") |
| .body(StringBody("Your gRPC Request Payload Here")) |
| .check(status.is(200)) |
| ) |
| setUp(scn.inject(atOnceUsers(10)).protocols(grpcConf)) |
| } |
Running the Gatling Performance Test
You can run the Gatling test using the following command:
./gatling.sh -s CalculatorSimulationGatling will generate detailed reports and metrics to help you analyze the performance of your gRPC service.
Conclusion
Performance testing is essential to ensure your gRPC services can meet the demands of real-world traffic. In this comprehensive guide, we set up a simple gRPC service and client and performed performance tests using Locust and Gatling.
Happy Load Testing 🔖